In the face of proliferating cyber threats, CTOs are increasingly asked to get involved in cybersecurity management, especially when the CISO/CSO role is absent.
However, with conflicting priorities, limited workforce, and finite budgets, it’s often hard to determine the best course of action.
Our team suggests focusing on the following cybersecurity trends to achieve early, tangible outcomes and secure greater stakeholder support for a well-rounded cybersecurity program.
Cybersecurity Trends For Short-Term Gains and Long-Term Advantage
Corporate cyber-resilience takes time. To build a staunch security perimeter, you need to introduce process improvements, people management initiatives, and technology innovations.
Moreover, your cybersecurity program must be proactive, not reactive, meaning that it has to prevent cyber attacks and breaches from happening rather than solely improve your incident response speeds and abilities to deal with present-day threats. Because the stakes are getting higher in terms of financial losses.
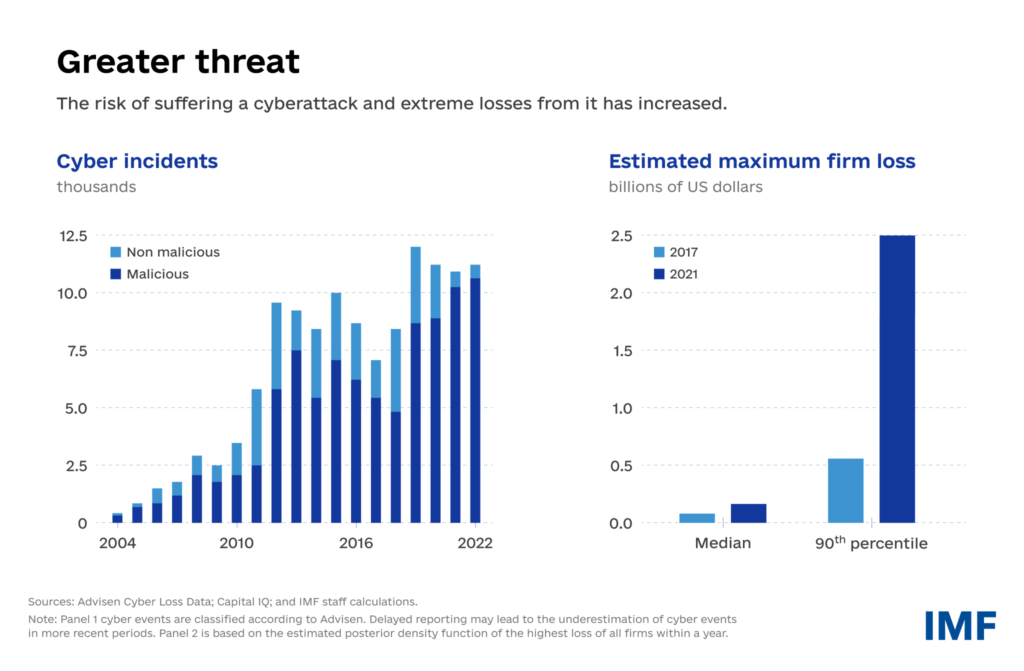
Source: IMF
To design an effective cybersecurity program that protects your company today and prepares it for tomorrow’s threats, we recommend that CTOs focus on the following six areas:
- Zero trust security model adoption
- Human-centric security design
- Multi-cloud security and risk management
- AI and machine learning for cybersecurity
- Security of AI systems and applications
- Cybersecurity workforce upskilling
Zero Trust Security Model
Zero Trust model requires all users, inside or outside the organization’s network, to be authenticated, authorized, and continuously checked for security configurations and posture before accessing applications and data. It’s backed by well-established standards like NIST 800-207 and CISA’s Zero Trust Security Model.
A traditional perimeter-based security model prevents threats from breaching the network perimeter. The Zero Trust model does that and promotes extra controls for data security inside the network, including firewalls, access and identity management (IAM) tools, public key infrastructure (PKI), security information and event management (SIEM) solutions, and enforced policies to control user and device behavior inside the network.
From the beginning, zero trust requires every user to verify their identity, thereby authenticating users and regulating access to corporate resources. It also uses advanced access controls to strengthen authentication for network devices and servers.
Zero Trust enables monitoring user behaviors and enforcing policies to prevent risks posed by distributed operations, such as remote workforces, BYOD policies, hybrid cloud services, API-based connectivity, and shadow IT.
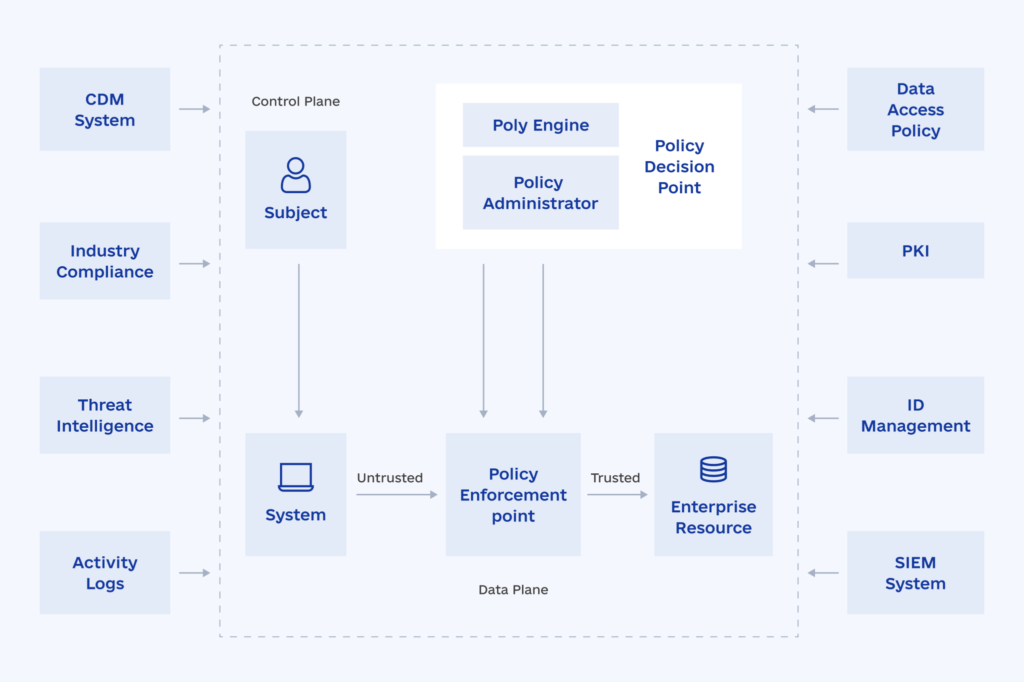
Source: Oracle
According to Gartner, 63% of companies globally have implemented a zero-trust strategy, addressing half or less of an organization’s environment and mitigating one-quarter or less of overall enterprise risk.
The Zero Trust model requires new cybersecurity expertise and investments in the right technologies, but it drives tangible outcomes. After adopting it, Akamai consolidated its security technology portfolio, eliminating legacy technology and reducing IT appliance and process overhead for new employees and authorized third parties. The company also reported cost reduction due to more efficient IT resource allocation and greater employee productivity.
Human-Centric Security Design
Six in ten CTOs believe human error is the biggest cybersecurity threat facing their organization.
Indeed, a lot of hacking tactics exploit the “human factor” — employees’ gullibility, inexperience, or nonchalance. Vulnerabilities also arise due to staff’s reluctance to comply with security policies like using two-factor authentication or strong passwords. Likewise, many people lack awareness about the dangers of opening suspicious attachments or installing unauthorized apps on their devices.
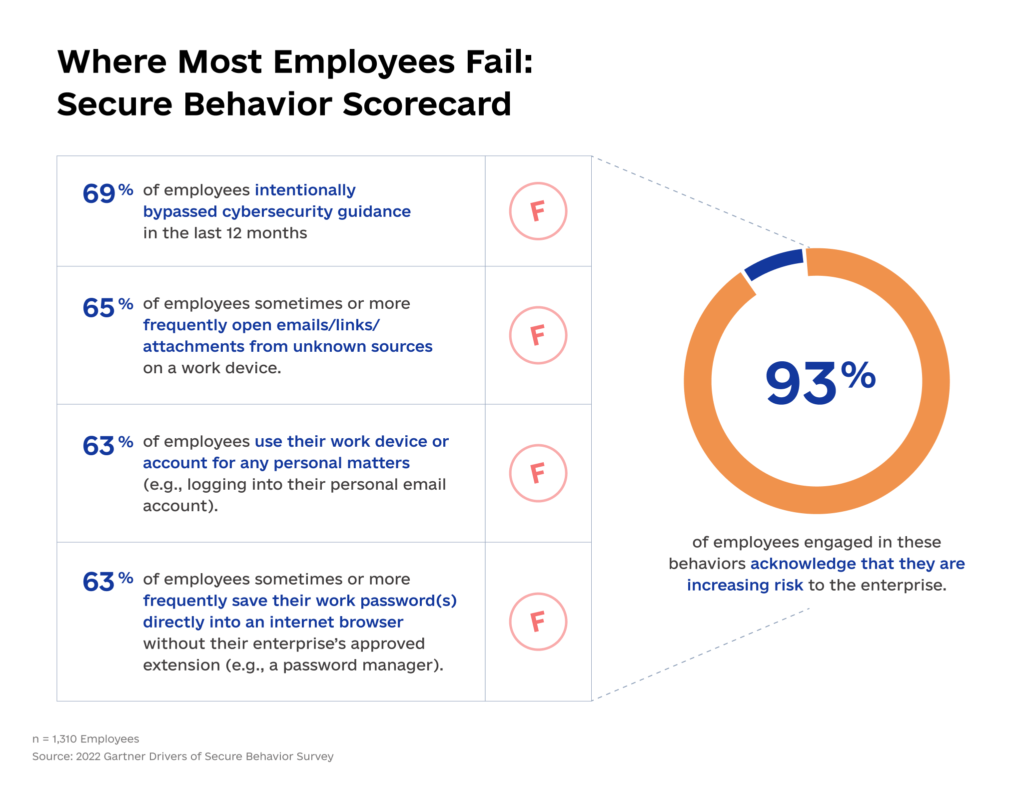
Source: Gartner
Employees must be the first line of defense, not the easiest leeway for hackers. Hence, your cyber program must drive measurable behavior change, not just promote checkbox compliance.
In 2023, NIST presented a Human-Centered Cybersecurity Program — a new security paradigm designed to “champion the human in cybersecurity”. Apart from addressing the usability of security technologies, it also promotes understanding and adapting to human behavior and psychology.
Instead of strict policies and punitive action, human-centric cybersecurity addresses individual needs and provides ongoing support to employees. It assumes the usage of user and entity behavior analytics (UEBA) to understand workforce behavior and its root causes. UEAB data helps identify policy and process shortcomings and design better controls. On a higher level, UEAB also aids in threat detection and ongoing security monitoring.
Based on the established behavioral baseline, you can design better role-based access control (RBAC), granting users the right degree of privileges and access permissions. A good RBAC mirrors your organizational structure. Establish different security roles based on the users’ functions and responsibilities and link these to specific security rights. Each role must have just enough permissions, following the principle of least privilege. Introduce role hierarchies to allow lower-level roles to inherit permissions from higher-level roles, simplifying access rights management. Popular IAM solutions like Microsoft Entra ID (former Azure Active Directory), Okta, and CyberArk allow easy automated implementation across the organization and ongoing policy fine-tuning from one interface.
Lastly, consider implementing passwordless authentication. Password reusing is a common reason for breaches, while constant password resets add extra work to your IT service desk and create user frustration. Passwordless methods like FIDO2 security keys, magic links, and biometrics are more user-friendly and secure. Adopters report 2.6X faster sign-in times and 25% fewer password reset requests from users.
These human-centric security design principles eliminate cybersecurity-induced friction, promote secure employee behaviors, and help reduce the risks of cyber breaches.

Multi-Cloud Security and Risk Management Strategy
Multi-cloud is now the dominant operational model, used by 89% of businesses. Indeed, this approach has many advantages — access to best-of-breed technologies, improved latency, and enhanced disaster recovery options among others.
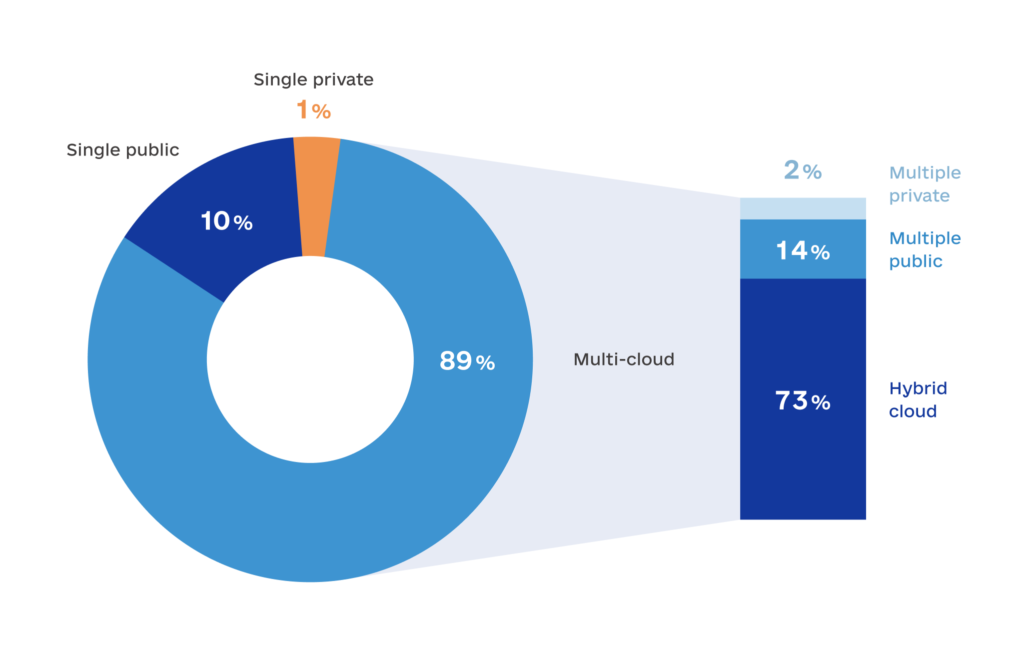
Source: Flexera
Yet, multi-cloud operations also pose new security risks. A 2024 State of Multi-Cloud Security Report by Microsoft found some glaring problems:
- Identity control. Microsoft Entra Permissions Management found 209 million identities across its customers’ clouds in 2023. Among the 51,000 permissions granted (up 22% from 2022), only 2% were used and 50% were high-risk.
- Cloud-native application and infrastructure security. In 2023, 65% of cloud code repositories had source code vulnerabilities for an average of 58 days. Moreover, the average company had 351 exploitable attack paths.
Businesses must do more to secure multi-cloud environments. CTOs could address the problems by implementing DevSecOps practices, which shift security to the software planning, design, development, and testing stages. A shift to the left improves alignment between development, QA, DevOps, and security teams on work processes and objectives. This ensures new cloud applications are developed in consideration of potential threat vectors, security vulnerabilities, and compliance requirements.
When shifting security left (towards the beginning of the SDLC), teams can identify potential security risks early on and build for every integration into the CI/CD pipeline. Teams automatically check for software dependencies and change impacts on the security performance. Apart from the standard unit and integration testing, DevSecOps promotes static application security testing (SAST) for every new build and container scanning. On the deployment side, DevSecOps promotes Dynamic Application Security Testing (DAST) — a type of black-box testing designed to probe running applications for potential vulnerabilities. OWASP has a detailed guide that further explains the key principles of DevSecOps.
At the infrastructure level, better multi-cloud cloud security posture management (CSPM) is necessary. Lack of visibility into multi-cloud environments leads to bloated permissions, unprotected workloads, resource inefficiency, and compliance issues, magnifying security risks. CSPM tools like Azure Arc unify security and compliance management across clouds by establishing a centralized resource inventory. It also helps monitor all connected clouds, distribute policies, perform patch management, and monitor cloud costs.
AI and Machine Learning for Enhanced Cybersecurity
Cyber security teams are understaffed and overworked. Seven in ten security specialists work weekends globally, according to a BitDefender survey. Long hours and high stress increase the teams’ intention to quit: 71% of UK cybersec professionals plan to look for a new job in 2024.
CTOs risk losing critical cybersecurity competencies. Rampant tech talent shortages also delay hiring times, meaning that many roles can be left unfulfilled for months unless you’re using an alternative approach like strategic vendor partnerships.
AI and machine learning (ML) cybersecurity solutions can reduce the mounting workloads security teams face by streamlining menial work. For 48% of security professionals, AI adoption is the top initiative for 2024, and here’s how they plan to use the technology.
- Alert prioritization. Security specialists face hundreds of alerts daily, many with low-value information due to outdated, overmatched, or over-sensitive system heuristics. This leads to alert fatigue, detachment, delayed responses, and overlooked threats. Half of companies plan to use AI for cybersecurity alert prioritization. Algorithms can triage alerts based on severity, potential impact, and relevance, helping teams focus on critical areas first.
- AI-assisted cyber threat intelligence. AI/ML solutions process large security telemetry data volumes and provide human teams with more accessible insights. New-gen AI assistants like Security Copilot, FortiAI, and Elastic AI assistants help query data with spoken commands and assist in case investigation with prompts.
- AI-enhanced SAST: Continuous static application security testing is an important DevSecOps principle. Yet developers often struggle with using security technology to assess their code. 45% think development teams will benefit from using AI for security reviews. GitHub introduced a code scanning autofix feature that provides an AI-suggested code fix alongside an alert directly in a pull request. Users can review the vulnerability explanation and the fix suggestion, specific to their use case, and decide on the next steps.
AI also has immense value for threat detection and prediction. Algorithms can be tuned to identify suspicious hostnames, IP addresses, and file hashes, suggest new rules, based on known cyber-attack patterns, and supply extra intelligence for Tactics, Techniques, & Procedure Reports (TTP). Half of the MixMode survey respondents said AI adoption improved their security posture by better-prioritizing threats and vulnerabilities, and 46% say AI tools help identify application security vulnerabilities more effectively.
Security of AI Systems and Applications
AI adoption spans well beyond the security function. Almost three-quarters of businesses are adopting generative AI fast or very fast, with 66% implementing it across functions. Greater accessibility of AI systems can boost productivity. However, AI systems can also amplify existing security risks or create new ones.
AI systems must be properly secured to prevent privacy and copyright breaches, data leakage, and direct adversarial attacks. The French National Commission on Informatics and Liberty (CNIL) outlined the main risk factors for the security of AI systems:
- The nature of data, submitted to an AI system (e.g., sensitive corporate data or personal user information)
- Control over the models, toolchain, and data (e.g., open-source models may contain compromised components; fine-tuning processes may introduce potential security flaws to the system, etc.)
- System access modalities (e.g., open-source distribution of the model, web access interface, or SaaS access increase the attack surface)
- The intended use context for the AI system: (e.g., an AI credit scoring solution will require more input to ensure its robustness versus a gen AI tool for generating presentation template).
The multi-dimensionality of this risk is reflected in emerging AI regulations (mentioned in our Generative AI trends post). Regulators are adapting compliance requirements based on the AI system’s intended use and potential risks.
The baseline for AI security is continuous monitoring. Implement AI observability dashboards to supervise model performance in training and production. Tools like Grafana and Prometheus collect telemetry data across the model lifecycle. Precisely, track key metrics like:
- Data quality, volume, distribution, drift, and dependencies
- Infrastructure utilization and saturation rates
- Model accuracy, precision, recall, and explainability
- For deployed models — availability, latency, reliability,
Additionally, you should integrate automatic data quality checks and privacy controls into data ingestion pipelines for all incoming data. Similarly, ensures protection of the data storage. Use firewalls, encryption, and secure data transfer protocols to minimize the odds of any leaks.
Comprehensive monitoring helps detect both drift in model performance as well as signs of malicious intrusion.
Cybersecurity Workforce Upskilling
Novel threats and security technologies demand new staff competencies. Over one-third of C-suite leaders identified cybersecurity and AI as top investment areas for staff training this year. Role-based, ongoing cyber awareness training should be part of your human-centric security program for business users.
Technical staff, in turn, could benefit from more advanced security certification programs. Almost 90% of leaders would be willing to pay for employees to get certified in cybersecurity. Certified professionals bring new knowledge to your organization and help discriminate best practices across the workforce.
Working with a strategic technology partner is another option for obtaining missing cybersecurity competencies. An experienced advisory team can help implement new security architectures and processes for threat detection, investigation, and prevention. For instance, at 8allocate, we help businesses implement threat intelligence collection systems and proactive security measures as part of a custom-built security architecture. In addition, our team can provide security awareness training to educate your workforce on best practices and adopt appropriate behaviors. This way, you get air-tight protection against all threats without competing for scarce security talent.
Final Thoughts
Proactive, zero-trust cyber security is supplanting reactive, perimeter-based measures.
CTOs can reduce mounting pressures from frequent security scares, long incident response times, and high program costs by implementing a new architecture, where security processes and policy enforcement are (semi-)automatic and analytics cover the entire IT estate.
While adopting these latest cybersecurity trends certainly requires hefty initial investments, proactive programs are also bringing measurable ongoing ROI in the form of reduced downtime, streamlined compliance, higher workforce productivity, and minimal chances of suffering a data breach.
Get in touch with the 8allocate team to learn more about building long-term cyber resilience.

Frequently Asked Questions
Quick Guide to Common Questions
Why is cybersecurity a top priority for CTOs today?
As cyber threats evolve, CTOs are taking on greater responsibility for security, especially in companies without a dedicated CISO. Cybersecurity is no longer just about protecting data—it ensures business continuity, regulatory compliance, and resilience against emerging risks. A proactive approach is essential to prevent breaches before they happen.
What is the Zero Trust security model, and why should companies adopt it?
Zero Trust operates on the principle that no user or device should be trusted by default, even if they are inside the corporate network. Every access request is continuously verified, reducing the risk of unauthorized access and insider threats. Unlike traditional perimeter-based security, Zero Trust assumes that breaches can happen anytime and ensures that security measures remain active across all environments.
How can businesses implement Zero Trust security effectively?
A successful Zero Trust strategy requires strong identity and access management, continuous monitoring of user behavior, and strict authentication controls. Companies must enforce multi-factor authentication, segment their networks to limit lateral movement and implement real-time security analytics to detect potential threats.
What role does human behavior play in cybersecurity, and how can companies reduce risks?
Human error remains one of the biggest causes of security breaches. Employees often reuse passwords, fall for phishing scams, or bypass security measures for convenience. A human-centric security approach focuses on making security practices intuitive and non-intrusive. Using passwordless authentication, monitoring behavior with analytics, and integrating role-based access controls can significantly reduce human-related security risks.
How does the rise of multi-cloud environments affect cybersecurity?
Many organizations now use multiple cloud providers, leading to security challenges such as fragmented identity management, inconsistent policies, and visibility gaps. Cloud misconfigurations are among the leading causes of breaches. To improve security, companies must unify their cloud security posture, standardize identity and access policies, and implement automated compliance monitoring across all cloud environments.
How can AI enhance cybersecurity?
AI is transforming cybersecurity by automating threat detection, analyzing vast amounts of security data, and identifying suspicious behavior in real time. It helps prioritize security alerts, reducing the burden on security teams and allowing faster responses to critical threats. AI-driven security solutions can detect vulnerabilities before they are exploited, providing an additional layer of protection against sophisticated cyberattacks.
What security risks are associated with AI itself?
AI-powered systems can introduce new vulnerabilities, such as data poisoning, adversarial attacks, and unintentional biases in decision-making. Protecting AI applications requires robust model governance, continuous performance monitoring, and strict controls on data access. Organizations must ensure that AI models are trained on high-quality data and regularly audited to prevent potential exploitation.
Why is cybersecurity workforce upskilling essential?
With cyber threats evolving, organizations need skilled professionals to stay ahead. However, the talent shortage in cybersecurity is a growing challenge. Investing in employee training, supporting cybersecurity certifications, and leveraging external experts can help businesses bridge the gap. AI-driven security tools can also reduce reliance on manual security processes, easing the burden on existing teams.
How can CTOs balance cybersecurity investments with business needs?
Security investments must align with business objectives without slowing innovation. By focusing on foundational security strategies such as Zero Trust, AI-driven threat detection, and proactive risk management, CTOs can strengthen cybersecurity without disrupting operations. Demonstrating the ROI of security initiatives—such as cost savings from breach prevention and improved compliance—helps secure executive buy-in.